Here’s a basic diagram of a standard proxy server setup:
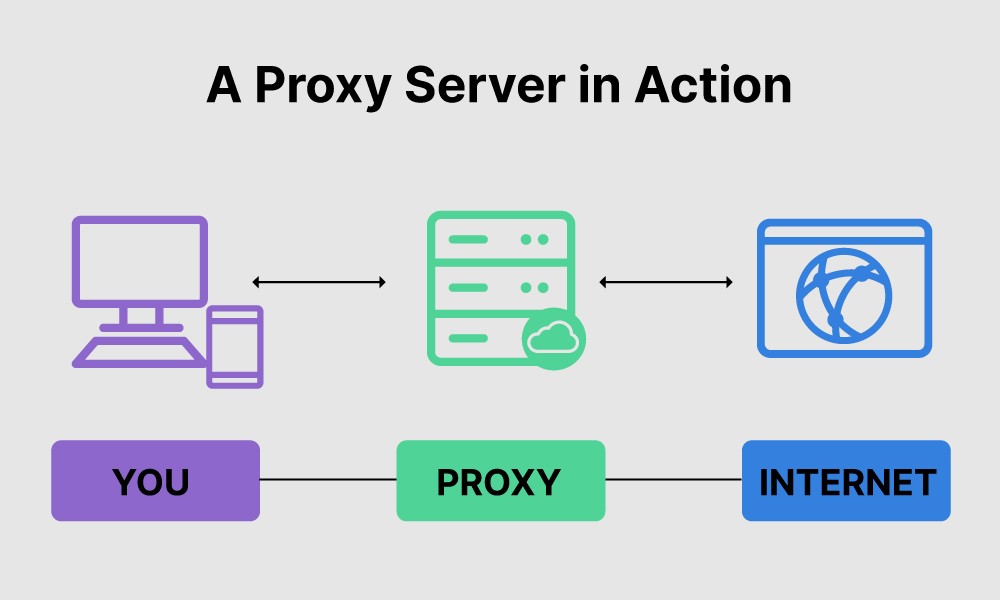
In this setup:
- Client: A user’s device (computer, smartphone, etc.) that initiates a request to access a resource on the internet.
- Proxy Server: A dedicated server that acts as an intermediary between the client and the actual web server.
- Web Server: The server hosting the requested resource (e.g., a website, image, file).
How it works:
- The client sends a request (e.g., to load a webpage) to the proxy server.
- The proxy server receives the request and forwards it to the appropriate web server.
- The web server processes the request and sends the requested resource back to the proxy server.
- The proxy server receives the resource and forwards it to the client.
Key points:
- The client is unaware of the actual location of the web server.
- The proxy server can cache frequently accessed resources to speed up future requests.
- Proxy servers can be used to filter content, improve security, and manage network traffic.
Additional components (not shown in the basic diagram):
- Firewall: A security device that can be placed between the proxy server and the internet to control network traffic and block unauthorized access.
- Load Balancer: A device that distributes incoming traffic across multiple web servers to improve performance and availability.
- DNS Server: A server that translates domain names (e.g., www.example.com) into IP addresses.
Note: This is a simplified diagram. Real-world proxy server setups can be more complex, depending on the specific requirements and environment.
Benefits of proxy servers
Proxy servers offer a range of valuable functions, enhancing both security and performance for users and network administrators. Here are some key functions:
1. Security:
- Anonymity: Proxy servers mask the user’s IP address, making it difficult for websites or third parties to track their online activities. This enhances privacy.
- Content Filtering: They can block access to specific websites or content types, such as malicious sites, adult content, or social media, ensuring a safer browsing experience, especially in controlled environments like schools or workplaces.
- Malware Protection: Proxy servers can act as a first line of defense against malware by scanning incoming traffic for threats and blocking them before they reach user devices.
- Intrusion Detection: They can monitor network traffic for suspicious activity, such as unauthorized access attempts or data breaches, and alert administrators.
2. Performance Enhancement:
- Caching: Proxy servers store frequently accessed content locally, reducing the need to fetch it from the original server each time. This speeds up page loading times for users.
- Bandwidth Management: They can prioritize critical traffic, such as business applications, while limiting bandwidth-intensive activities like streaming or large downloads, optimizing network resources.
- Load Balancing: In larger networks, proxy servers can distribute traffic across multiple servers, preventing overload and ensuring consistent performance.
3. Network Management:
- Access Control: Administrators can use proxy servers to control which users have access to the internet and what resources they can access, enforcing network policies and security measures.
- Traffic Monitoring and Reporting: Proxy servers can track network usage, identify bandwidth-intensive users or applications, and generate reports for analysis and troubleshooting.
4. Bypassing Geo-restrictions:
- By using a proxy server located in a different country, users can access content that is geo-blocked in their region.
In essence, proxy servers act as intermediaries, providing a layer of security, enhancing performance, and facilitating network management for both individual users and organizations.
Note: The specific functions of a proxy server can vary depending on its configuration and the type of proxy server being used (e.g., forward proxy, reverse proxy).
List of best free proxy servers
It’s not recommended to look for such risky option, here are some reasons to consider for moving away from free options:
- Rapidly Changing Landscape: Free proxy servers come and go frequently. Those that work today may be blocked or unavailable tomorrow.
- Security Risks: Many free proxies are compromised, potentially exposing your device to malware or misuse.
- Performance Issues: Free proxies often have slow speeds, low uptime, and limited bandwidth, making them unreliable for most tasks.
Where to Find (and Use with Caution):
- Online Proxy Lists: Websites like “Free-Proxy.cz” and “ProxyNova” provide constantly updated lists. However, these lists often include proxies that are already blocked or unreliable.
- Proxy Search Engines: Some search engines specialize in finding free proxies. However, the quality of these proxies is highly variable.
Important Notes:
- Test Thoroughly: Before using any free proxy, test it to ensure it’s working and not malicious.
- Limit Usage: Avoid using free proxies for sensitive activities or large amounts of data.
- Consider Alternatives: For reliable and secure proxy use, it’s generally recommended to use paid services or a VPN.
Disclaimer: Using free proxies can carry risks. I strongly advise against using them for any activities that require high security or reliability.
Instead of relying on free proxies, consider these safer alternatives:
- VPN Services: Offer robust encryption, better privacy, and often faster speeds than free proxies. Many reputable VPN providers offer free trials or limited free plans.
- Paid Proxy Services: Provide higher quality, more reliable proxies with better performance and support.
Remember to prioritize your online security and privacy. Use caution when dealing with free proxies and consider safer alternatives whenever possible.
List of best premium (paid) proxy servers
Here’s a list of some of the best premium (paid) proxy server providers, known for their reliability, performance, and security:
- Smartproxy
- Large pool of residential IPs (over 40 million)
- Rotating IPs for enhanced anonymity
- Ideal for web scraping and accessing geo-restricted content
- Affordable pricing
- Oxylabs
- High-quality data center and residential proxies
- Excellent for data collection and scraping
- Robust infrastructure and advanced features
- Bright Data (formerly Luminati)
- Wide range of proxy solutions for various needs
- Global reach and extensive network
- Ideal for businesses and enterprise-level users
- ProxyMesh
- Rotating residential proxies for enhanced privacy
- Large IP pool and global coverage
- User-friendly interface and reliable performance
- ScraperAPI
- Simple API for easy integration into web scraping projects
- High-quality residential proxies and automatic IP rotation
- Ideal for developers and businesses
- MyIPHide
- Anonymous browsing and secure connections
- Residential and data center proxies available
- Ideal for individuals and small teams
- Storm Proxies
- Affordable pricing and reliable performance
- Ideal for small-scale users and personal needs
- Hidester
- Easy-to-use interface and beginner-friendly
- Residential and data center proxies available
- Good for general web browsing and accessing geo-restricted content
- GeoSurf
- Premium residential proxies for bypassing geo-restrictions
- Large IP pool and global coverage
- Ideal for accessing content from specific locations
- NetNut
- Business-oriented proxy solutions
- High-performance proxies for demanding applications
- Ideal for enterprise-level users and large-scale operations
Note: This list is not exhaustive, and the best provider for you will depend on your specific needs and budget. It’s recommended to research and compare different providers before making a decision.
Remember: Always prioritize security and ethical use when choosing and using a proxy service.
Most common types of proxy servers
Based on Traffic Flow:
- Forward Proxy:
- Most common type.
- Clients on a local network use it to access the internet.
- Hides client identities from the websites they visit.
- Often used in corporate networks for security and content filtering.
- Reverse Proxy:
- Acts as a gateway for external clients to access internal servers (like web servers or databases).
- Improves security by shielding internal systems from direct external access.
- Can also handle load balancing and caching.
Based on Anonymity Level:
- Transparent Proxy:
- Doesn’t hide the client’s IP address.
- Primarily used for network management and monitoring.
- Anonymous Proxy:
- Hides the client’s IP address but reveals that a proxy is being used.
- Elite Proxy:
- Hides the client’s IP address and also masks the fact that a proxy is in use.
- Provides the highest level of anonymity but can be more difficult to find and configure.
Based on Protocol:
- HTTP Proxy:
- Handles HTTP and HTTPS traffic.
- Most common type for web browsing.
- SOCKS Proxy:
- Supports various protocols, including HTTP, FTP, and Telnet.
- More flexible than HTTP proxies.
Based on Usage:
- Residential Proxy:
- Uses residential IP addresses (from real home internet connections).
- More difficult to detect as bots, making them ideal for tasks like web scraping and social media automation.
- Data Center Proxy:
- Uses IP addresses from data centers.
- Generally faster but easier to detect.
- Rotating Proxy:
- Cycles through a pool of IP addresses, changing the IP used for each request.
- Helps avoid detection and improve anonymity.
This is not an exhaustive list, but it covers the most common types of proxy servers you’ll encounter. The best type of proxy server for you will depend on your specific needs and priorities.





Leave a Reply